Foxconn has been targeted by hackers again.
Recently, according to media reports, Foxconn’s parent company, Hon Hai Group’s Mexican factory, was attacked by the extortion software “doppel paymer”. Hackers steal some unencrypted files and encrypt them.

Hackers claim that there is no other way to stop the attack except decrypting the key, otherwise the files will be damaged!
However, Foxconn responded today that:
Its American factory has been attacked by network blackmail virus recently. At present, its internal information security team has completed the security update of software and operating system, and improved the level of information security protection. In this attack, the network of the affected plant area is gradually returning to normal, which has little impact on the overall operation of the group.
Don’t get the decryption key without paying the ransom
Just at the end of Thanksgiving, Foxconn received a blackmail from a hacker.
The letter said:
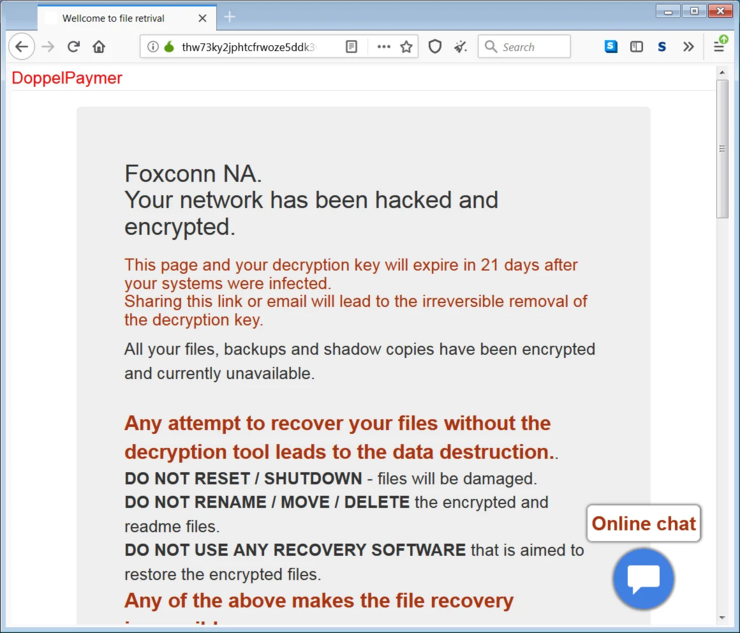
Your company’s network has been hacked and encrypted.
This page and your decryption key will expire within 21 days after your system is infected.
Sharing this link or email will cause the decryption key to be irreversibly deleted.
All of your files, backups, and shadow copies are encrypted and are currently unavailable.
Any attempt to recover a file without a decryption tool will result in data corruption.
Finally, the hackers also warned Foxconn:
Do not reset / shutdown file will be damaged;
Do not rename / move / delete encrypted and readme files;
Do not use any recovery software designed to recover encrypted files.
At the same time, the hackers also put forward the terms of the deal. In the blackmail letter, the hackers mentioned that they demanded a ransom of 1804.0955 bitcoin, which is about 34686000 US dollars at today’s bitcoin price
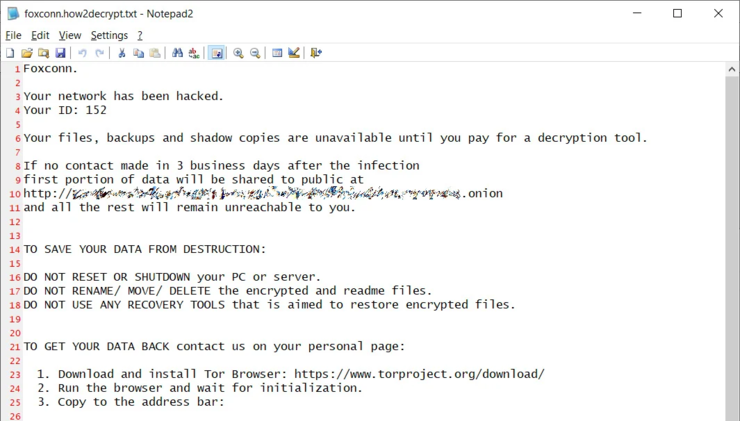
The hackers also said they had encrypted about 1200 servers, stolen 100 GB of unencrypted files, and deleted 20tb to 30tb of backup content.

We’re encrypting the Na part, not the entire Foxconn, which has about 1200-1400 servers, not workstations. They also had about 75tb of misc backup, and we destroyed about 20-30tb. ”
What did hackers attack?
According to foreign media bleeping computer, Foxconn’s ctbg MX production facility in Ciudad Juarez, Mexico, was under attack.

The facility opened in 2005 and is used by Foxconn to assemble and transport electronic equipment to all parts of South and North America.
Since the attack, the official website of the production facility has been paralyzed and error messages are being displayed to visitors.
According to the leaked data released by hackers, the leaked data includes general business documents and reports, but does not contain any financial information or personal details of employees.
How lethal is doppelpaymer?
According to public data, doppelpaymer is a new variety of bitpaymer blackmail software. At the same time, doppelpaymer has at least eight variants, which gradually expand their respective feature sets.

According to security researchers, such malware first steals data and then sends ransom messages to victims, rather than encrypting and locking data in place, as traditional ransomware does.
It has been active since mid-2019. In March this year, Visser, a US precision parts manufacturer, was attacked by this blackmail software, accidentally leaking sensitive documents related to Tesla, Boeing, SpaceX and other companies.
Doppelpaymer blackmail software was first discovered in June 2019. It is mainly spread through RDP brute force cracking and spam. There is a self decompressing file in the email attachment. After running, the blackmail software program is released and executed.
After the self extracting file is run, create the graimin folder in the% users% directory and release the name p1q135no. Exe After encrypting the file, the suffix named “. Locked” is added after the original file name, and “. Readme2” is added after the original file name in the directory of each encrypted file unlock.txt ”The blackmail includes the blackmail description, tor download address, payment address, data information and email contact information.
Doppelpaymer ransomware uses “RSA + AES” algorithm to encrypt files, uses multithreading to quickly encrypt files, and uses command ARP – a to resolve the address resolution protocol (ARP) table of the victim system. The specific operations are to delete shadow copies, disable repair, and delete the backup directory of the local computer.
The encrypted file cannot be decrypted until the key is obtained.
It seems that Foxconn is bound to pay $34 million to plug this security risk.
Not for the first time
But in fact, this is not the first time Foxconn has been hacked.
In February 2012, a hacker group calling itself “swaggsec” announced on twitter that it had used the loophole to break through the internal network of Foxconn, the world’s largest manufacturer of electronic accessories, and obtained email and password information of a large number of Foxconn customers, including Microsoft and apple. They also published an open letter saying that this was punishment for Foxconn’s inhumane employment environment.

Swaggsec claims that it seized an unrepaired vulnerability in Foxconn employees’ IE browser, easily bypassed the firewall and intruded into the intranet as an administrator. They published a large number of Foxconn internal information in the document, including user names, passwords and some financial information that can log in to multiple intranet servers. These servers have been shut down urgently.
In 2015, researchers at Kaspersky laboratory, a Russian information security company, revealed that Foxconn’s computer system had been hacked by a group of Israeli hackers.
Kaspersky said: the organization has implanted a piece of malicious software into the system developed by Foxconn engineering, and there is evidence that: the hacker entered through the internal authority pass, specifically through the defense weak link; or has he stolen the pass? It doesn’t matter. The main thing is that invasions are purposeful.
In 2016, Foxconn’s former employees intruded into Apple’s system by installing a wireless router inside. The wireless bridge was used to connect the wireless signal bridge to the outside of the factory. The bridge signal was directly connected to the intranet of the enterprise. A large number of information were refreshed, and a large number of codes were copied and modified. The illegal income was more than 3 million yuan.
It seems that Foxconn will continue to strengthen the security system.
As for how to enhance the ability to prevent the extortion virus, Lei Feng network (official account: Lei Feng net) also asked the experts of network security, they think that we should start from the following six points:
1. Timely repair system vulnerabilities, and do a good job in daily safety operation and maintenance.
2. Adopt high strength password to eliminate weak password and increase the difficulty of blackmail virus invasion.
3. Back up important data regularly. It is recommended to use a separate file server for isolated storage of backup files.
4. Strengthen security configuration and improve safety baseline.
5. Improve the safety awareness of employees, do not click on the email of unknown source, and do not download software from unknown websites.
6. Choose anti-virus software with strong technical ability, so as to avoid damage in the case of increasingly fierce extortion virus attack.

