How long does it take a car thief to steal your new Tesla Model x?
The answer is within three minutes.
You may think it’s impossible, but in fact, in the eyes of hackers, it’s just a child.
On November 24, according to foreign media reports, a security researcher showed serious vulnerabilities in Tesla Model x keyless entry system
Through this vulnerability, hackers can use Bluetooth connection to rewrite the firmware of the vehicle key card, obtain the vehicle unlock code from the key card, and use it to steal a model X in a few minutes.
Any car thief who tries to read the car identification number (usually visible on the dashboard through the windshield) can exploit the holes, which are about 15 feet (4.57 meters) from the victim’s key chain, and the hardware kit required to implement the scheme costs only $300.
It’s a little bit tough.
What is the underlying principle?
It is understood that this “relay attack” is a trick commonly used by Tesla thieves in Europe and the United States, and many car owners have suffered greatly.
So, what is the principle of this theft?
Lennert Wouters, a security researcher, found that model X’s keys lacked the so-called “code signing” for firmware updates.
Code signing is the digital signature that software developers can sign their software code. Users can identify the publisher of the software and whether the software has been tampered with in the transmission process through the code signature service.
Tesla has designed a model x key card, which wirelessly connects to the internal computer of model X and receives wireless firmware updates through Bluetooth. However, it does not confirm that the new firmware code has Tesla’s unforgeable encrypted signature.
In other words, it is this defect that gives the thief an opportunity.
Therefore, the security personnel try to use their own computer with Bluetooth radio to connect to the key card of the target model x, rewrite the firmware, and use it to query the security chip in the key card that generates the unlocking code for the vehicle.
But it’s not easy. Because the Bluetooth radio of the model x smart key will “wake up” for a few seconds only when the battery of the smart key is removed and put in again.
However, the computer responsible for the keyless entry system in model X has a component called the body control module (BCM), which can also perform Bluetooth wake-up commands.
How easy are Tesla keys to cheat? In just three minutes, your model x could be hacked away

BCM is an embedded system, which can control the load driver and coordinate the activation of automotive electronic units.
The microcontroller and connector integrated into the BCM constitute the central structural unit of the system responsible for the control part. The operation data is transmitted to the control module through the input device.
After the module processes the data, the response signal is generated by the integrated output device (including relay and solenoid). Through the output device system, the BCM coordinates the work of various electronic systems.
By buying the model X’s BCM for $50 to $100 on eBay, you can spoof low-frequency radio signals sent to the key card. (although the initial wake-up command must be sent from a close range radio range of about 15 meters, if the victim is outdoors, the rest of the firmware update technique can be performed hundreds of feet away. )
In addition, the BCM obtains a unique identification code from the last five digits of the vehicle identification number of the electric vehicle. Hackers can read the numbers from the windshield of the target electric car and use it to create a code for their pirated BCM in just 90 seconds.
With that done, hackers can now unlock your model X.
So, how do you drive your car?
Security researchers also conducted further experiments.
First, after unlocking the model x, the security researcher plugs his computer into a port that allows the computer to send commands to the electric vehicle’s internal component network, known as the CAN bus, which includes This port can be accessed through a small panel under the display screen, and it only takes a few seconds. There is no need for tools, just pull out a small storage container on the dashboard.
In this process, security researchers also found that the BCM did not actually check the authenticity of the certificate, which means that after forging the fake key, hackers can drive away as long as they pass the verification of the BCM.
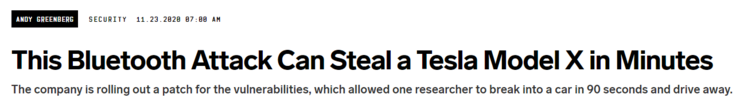
Security researchers also showed off kits to complete the attack: a raspberry PI minicomputer, a second-hand model x BCM, a key card, a power converter, and a battery.
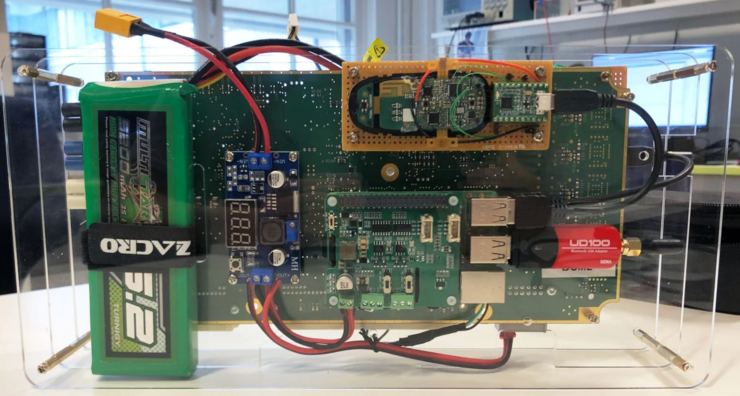
The entire kit can send and receive all the necessary radio commands from a backpack for less than $300.
In response, Tesla also responded urgently that the patch may take nearly a month to launch on all vulnerable vehicles, so model x owners should ensure that any updates provided by Tesla are installed in the next few weeks to prevent hackers.
Tesla’s security is not a day or two
The importance of this study is to reveal the actual end-to-end attacks on vehicles.
It should be noted that this is not the first time Lennert Wouters has disclosed a vulnerability in Tesla’s keyless entry system. He has found two password leaks in Tesla Model s keyless entry systems, which also allow for radio based electric vehicle theft. He doesn’t think Tesla’s keyless access security method is particularly unique. Similar systems may be equally vulnerable.
Just before model X was exposed, a video about Tesla sparked a discussion on the Internet. In the video, the photographer’s dash cam records a picture of a Tesla skylight being lifted up in front of the camera, which almost hits the photographer’s vehicle.

But this response seems to have failed to buy into most of the net. Some netizens pointed out that there is a precedent in foreign countries that the skylight of Tesla has been lifted. In October this year, a Tesla owner in the United States once sent an article saying that the panoramic skylight suddenly fell off and the model y became a “convertible” in seconds.
There are also reports that Tesla owners may encounter the problem of aging NAND memory chips, which may lead to “a series of problems in some Tesla vehicles, from the failure of the rear-view mirror camera to the lack of turn signal ring tones and other audio alarms.”.
And similar security incidents continue.
Of course, technology always brings losses, but more importantly, it promotes the overall social progress. We hope that in a few years, we can travel in safer autonomous vehicles.
