Your iPhone may not be safe even if it’s lying there.
Ibeer, the latest security bug from Apple’s mobile phone can be completely controlled by hackers from Google zero project.

The whole attack process only takes two minutes, and the attacker gets the read and write permissions of kernel memory.
At the same time, it also means that attackers can read your email and other information, download photos, and even monitor and monitor users through the iPhone’s microphone and camera.
In order to achieve this attack, hackers exploit the vulnerability of Apple Wireless direct link (awdl) protocol, through which the functions of airdrop and the second screen of sidecar are realized.
The more serious consequence is that this vulnerability involves all iPhones and other IOS devices. Once this vulnerability is exploited by hackers, you know the consequences.
Fortunately, Apple has already uploaded a fix in May.
How do hackers attack your iPhone?
So how did this attack happen?
According to Ian beer, this attack is actually a kernel memory corruption vulnerability, which causes all IOS devices in the vicinity of the radio to restart, without user interaction, running arbitrary code on any nearby IOS device and stealing user data.
Moreover, the range of such attacks can be large if higher transmit power and sensitive receivers are used.
How to achieve it?
The breakthrough point of this vulnerability lies in the awdl protocol.
He found that a protocol called Apple Wireless direct link (awdl) was used on the iPhone, iPad, MAC and watch.
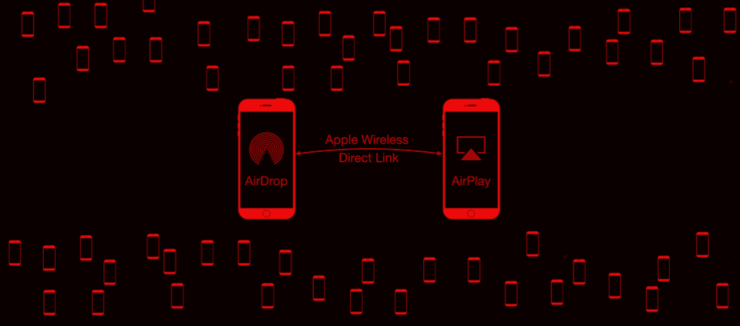
Awdl is not a custom radio protocol.
This is a protocol launched by apple in 2014 and plays a key role in the implementation of communication between devices in Apple ecosystem. Although most Apple end users may not be aware of the existence of the protocol, awdl is the core of some apple services, such as airplay and airdrop.
Awdl is activated by Bluetooth. This means that when a user is using Bluetooth, the awdl interface of all Apple devices around it will be activated, and hackers will take the opportunity to steal your information.
Of course, not everyone will turn on Bluetooth from time to time, so at this time, hackers need to find a way to force awdl on.
So it took Ian beer six months to do the experiment.
Since the wireless chip can only work on one channel at a time, awdl will use frequency hopping technology to jump to the working channel of en0 interface and awdl0 interface at different time slots. In addition, each time the awdl0 interface is activated, a new randomly generated MAC address is used.
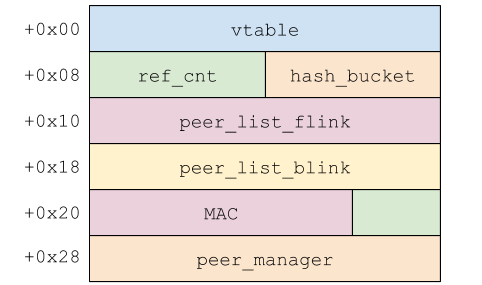
Therefore, LAN beer establishes a remote arbitrary memory read-write primitive to activate the awdl interface. After successful activation, the awdl buffer overflow can be used to access the device and run the implant program as root user. It can be seen that the read and write permissions of kernel memory can be obtained within seconds after startup.
After completing this step, the attack has basically been realized.
Then, when the attacker implants the program, he can call your information, including email, photos, messages, etc., and the process takes about two minutes.
And users have no perception of the process.
Seeing this, netizens in the comment area were also shocked
Soon, the information in my mobile phone was synchronized by others!!!
But fortunately,
“There is no evidence that these problems have been exploited by hackers.”.
So don’t worry too much.
Moreover, this vulnerability has been fixed as early as may this year, but he suggested that we should not ignore the attack power of hackers and install the upgrade as soon as possible.
Awdl protocol brings more privacy and security issues
In addition, he also mentioned in his research that awdl protocol has more privacy security issues.
Because Apple has never released any in-depth technical details about how awdl works. This in turn leads to few security researchers paying attention to the vulnerability or implementation error of awdl.
Therefore, in order to prove its security, in 2018, researchers reverse engineered the awdl protocol, then rewritten it as a C implementation and named it owl (open wireless link). Then use owl to test the real awdl protocol in various attack situations.
The results show that awdl brings a lot of hidden attacks from design defects to implementation vulnerabilities.
Specifically, there are four attack possibilities:
1. Long term device tracking attacks, despite MAC randomization, can display personal information, such as the name of the device owner (more than 75% of the experimental cases).
2. Aiming at the DoS attack of awdl election mechanism, the channel sequence of the target is deliberately out of synchronization, which effectively prevents communication.
3. Mitm attack intercepts and modifies files transmitted through airdrop, effectively allowing malicious files to be planted.
4. Two DoS attacks on Apple’s awdl implementation in Wi Fi driver. These attacks can cause Apple devices to crash nearby by injecting a specially designed framework. Attacks can target a single victim or affect all adjacent devices at the same time.
Of all these attacks, the awdl vulnerability that allows users to trace is the most worrying.
Using these vulnerabilities, researchers can obtain information from awdl connections, such as device host name, actual MAC address, even if MAC address randomization is turned on, AP of device connection, as well as device class and awdl protocol version. All of these details are enough to cause user tracking.
In addition, researchers warn that the same error could affect Android and other types of devices.
So it’s time for apple to pay attention to the security of awdl.


Unde explicabo et nulla ut et. Reprehenderit adipisci nostrum harum molestiae maxime repellat dolores est. Odit fugit distinctio illo sed asperiores.
Nemo eos et sint earum. Voluptate quo expedita dolor dolor adipisci ex blanditiis. Perspiciatis perferendis vitae dolorum. Delectus quas similique nihil veniam magnam neque accusantium. Est unde et corporis sit possimus dolor itaque ut.
Aut dolor dignissimos aut omnis necessitatibus aut. Qui porro fuga nihil molestias. Maxime qui aliquid dolores et in molestiae. Et ea quod qui dolor cupiditate sed et.